Ransomware is a type of virus/malware that restricts access to an infected computer (by encrypting the files) and requires the person pay a ransom to the malware operators to remove the restriction and gain access to those files again. The risk of ransomware attacks is an increasingly popular security concern for both home and corporate networks.
Yes, it’s as bad as it sounds (and expensive), and it’s definitely no fun recovering from an attack. Even if you haven’t seen or heard of any instances of this happening, it would be well worth spending a few minutes of your time getting up to speed on various ways to protect against them.
Over the last several years I’ve been involved with several support calls where end-users files and network servers have been compromised by a ransomware virus – and in nearly all cases, has resulted in restoring that compromised data from backups, or using other time-consuming techniques to recover the customer’s data. Preparation and adhering to industry best-practices is key in helping to minimize the risks and giving you the necessary tools for combating any potential ransomware attack on your network.
1. Firewall appliance with web filtering capabilities

FortiGate, Sonicwall, Untangle, and other UTM (Unified Threat Management) security appliances/firewalls all offer software features that provide a good first-line-of-defense against the risk of ransomware viruses gaining the ability to get into your network (by limiting what websites your end-users can access, and limiting what internet traffic can get to your company’s online resources).

This Wisconsin manufacturer needed to modernize its IT infrastructure to support rapid business growth.
Discover what they didNot only can a firewall with UTM capabilities limit your network’s attack surface, but it can also block or scan file downloads in real-time to determine if the file contains malicious code even prior to reaching the client’s computer anti-virus agent software. Also, in recent years, websites are increasingly standardizing on HTTPS (HTTP over SSL) to encrypt communications between the web server and the client’s web browser.
Consideration should be taken in whether SSL web filtering should be implemented to scan this type of encrypted traffic traveling over HTTPS to further protect your network.
2. Centralized anti-virus management server

An anti-virus solution from Sophos, McAfee, Avast, or other anti-virus software vendors can provide you with a centralized anti-virus management server/console. This gives the IT department the ability to report on, and get notified of, all active threats in your network – whether it is a local management server or a SaaS-based (Software as a Service) cloud anti-virus solution.
In more advanced (reactive) setups, certain triggers can even be programmed to disable or limit the network connectivity, and forcefully shut down the computer – essentially quarantining the device until you can visit the infected system and deal with the threat. To minimize the risk of Ransomware and other malware wreaking havoc on your files and data, staying up to date and current with your selected anti-virus solution is probably one of the most critical deterrent pieces.
3. Making sure that User Accounts have minimum rights

Ransomware attacks typically run under that particular end-users account (and security context). For this reason, it’s important to adhere to Principal of Least Privilege when assigning security permissions for end-users – assigning only the minimum permissions needed for that user to perform their necessary job duties and tasks.
The two most common configurations for setting up end-user account permissions on a workstation are:
- The user account is set up only as a member of the “Domain Users” security group. This basic level of access will prevent users from installing software on their computer and gaining access to system files, registry settings, and other important operating system resources. This level of access is the best method for minimizing the risk of ransomware.
- The user account is set up as a member of the “Domain Users” security group and is also added to the local “Administrators” security group on the workstation. This higher level of access is generally used to ease the burden on IT helpdesk technicians because it allows for the end-user to manually install software and drivers on their own. This level of access offers minimal security against malware and viruses and allows for a Ransomware program to embed itself within the operating system.
Finally, IT administrators should also be encouraged to follow the Principal of Least Privilege model and be strongly cautioned against using “Super User” accounts (accounts that are a member of the Domain Admin, or equivalent, security group) for their daily activities throughout the workday. If the IT Administrator’s machine gets infected by a Ransomware virus, or any virus for that matter, while using an account with Administrative-level privileges, then nearly everything on your network will be put at risk!
4. Setup correct file and folder level permissions
Just like having a good firewall appliance that limits your attack surface online, setting up correct file and folder level permission to your Network Shares (and the files and folders within) that end-users are given access to will substantially decrease your attack surface internally.
When configuring NTFS security and access to internal resources (such as Network Shares, folders, and files) you should provide permissions only to the specific users that require access to those resources. This will help block any potential Ransomware threats and viruses from spreading and accessing those resources.
As an example, if you have 3 department folders (Sales, Marketing, and Engineering) shared on your network, configure your NTFS permissions on those folders in the following way:
- Only Sales users are given access to the Sales department folder
- Only Marketing users are given access to the Marketing department folder
- Only Engineering users are given access to the Engineering department folder
Yes, it seems like common sense, but even the most experienced Network Administrators tend to forgo following best practices occasionally. Implementing strong NTFS permissions across your network shares, and spending time upfront architecting a good security policy, will lead to a more stable and secure network environment down-the-road.
5. Enable volume shadow copies on shared folders drives

Enabling Volume Shadow Copies on your server’s hard drives that contain Network Shares adds incremental protection to your data and files for your entire organization.
Depending on how you configure Volume Shadow Copies, any changes made to the file (in this scenario, a Ransomware program that parses and encrypts all your files) can easily be recovered from an earlier snapshot, even prior to the attack that encrypted the file(s). Volume Shadow Copy recovery is a feature built into the Windows Server operating system, and in the case of ransomware attacks, is even faster to recover from than restoring your data from your backup software!
[x_alert heading=”Helpful Tip” type=”info”]Using the Volume Copy Service may not be 100% fool-proof (ransomware and other malware techniques are always evolving) but it has been an extremely effective method in dealing with any these kinds of attacks.[/x_alert]
The easiest way to enable Volume Shadow Copies is to go into File Explorer, right-click on the hard drive that contains the shares, select the Shadow Copies tab, and configure it to suit your specific needs. Be sure to allocate enough hard drive space to protect your largest set of data accessible to one user account. Another good tip is to use Volume Shadow Copies along with folder redirections and roaming profiles to add a quick and efficient safety-net for all your client computers.
6. Setup file screening on network shares
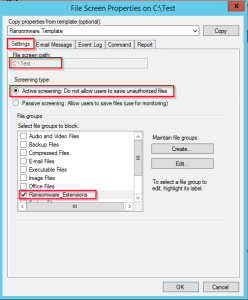
Setting up FSRM (File Server Resource Manager) on your primary file server has many benefits, including to helping minimize the risks of ransomware attacks.
In most environments, I tend to utilize FSRM to prevent end-users from wreaking havoc on your storage – I think we all know that individual who decides to copy his entire 2TB music collection onto his work computer. In the case of a ransomware virus infection, certain policies can be put in place to trigger actions when a known malware or virus attempts to encrypt files on that file server.
Many resources are available online to optimize FSRM for ransomware protection, and one FSRM script that seems to work well for many people is located here on Microsoft Technet.
7. End-user training, awareness, and common sense
Educating end-users is extremely important in helping to fight against the risk of ransomware attacks and other viruses. Here are few tips that end-users should be taught:
- Train users not to publish their company email address on websites, blogs, and when they sign-up for exhibitions. Search engines and other “bots” crawl the web and are programmed to grab valid email addresses and use them to their advantage.
- Use captchas on website forms to test whether form submissions are from valid humans and not submitted by another programmable means.
- Pull the plug – if a user suspects their computer was infected, pulling the power from their computer, or holding down the power button to turn it off immediately, will prevent ransomware executables from causing more harm.
- Train users not to open (but instead to delete, close, etc.) emails and attachments they think might be skeptical or unusual. A vendor, or customer, can easily re-send a valid email if it was deleted by mistake. Get end-users in the habit of reporting suspicious emails to the IT department, instead of opening them first!
- Security Awareness Training – there are several good organizations that can help offload the burden of end-user training as it relates to security awareness. KnowBe4 is one such service that aids your organization in training your staff to recognize phony phishing email campaigns and reporting this information back to the IT department.
8. Offline/offsite backups and security
Just like it’s common sense NOT to back-up a server to a 2nd partition on the SAME logical volume/array, it’s also common sense to have a backup policy that includes offline backup media that are rotated off-site in case there is an on-site disaster.
Disasters can come in many different and unexpected ways, including ransomware, fires, floods, theft, cyber threats – you name it, all have the potential to cripple any company and may cost hundreds of thousands of dollars in lost revenue and several years of company data in the process.
Depending on the size of your organization, your backup solution may include something as simple as several external-USB backup drives that someone rotates out on a regular basis, or the use of a NAS (Network Attached Storage) device located in a different part of the building or even located at a secondary site, or maybe the combination of a disk backup with duplicate tape-backups used for longer archival purposes, in combination with a secondary cloud-based backup solution.
The most important takeaway for Backup and Recovery is making sure your company has a valid (and tested!) backup solution in place that allows your organization the chance to recover from an unexpected attack and gives you peace of mind in the risk of ransomware getting a hold. And remember, recovering from a ransomware attack won’t be possible if your backup solution isn’t regularly taking successful/complete backups of your company’s data, so make sure someone is regularly reviewing your backup solution and software for success and addressing any backup failures in a timely manner.
9. Protect your cloud storage

Dropbox, Google Drive, One Drive are all “free game” for a system that has been compromised by a ransomware virus.
All these services offer an offline “cached” folder of the cloud account files and when a malware or virus hits, it will recursively parse through all the folders and files the victim has ownership/write access to and encrypt them. Once this cached folder becomes compromised, the cached copy then propagates to the files stored on the cloud account, and then back down to all the other devices you have set up to access the cloud service offline. Luckily most cloud-based storage services offer the ability to recover changed files up to a set amount of days.
For example, a free Dropbox account allows users to recover up to 30-days of changes. Many of these cloud storage providers even offer extended retention times for an additional cost.
10. Transition away from 3rd party email service providers

Consider moving away from 3rd party email service providers like GoDaddy, Dotster, 1and1, etc. that do not offer advanced anti-spam and anti-malware protection services.
Granted, you could always team-up your hosted email service with a SaaS-based anti-spam and anti-malware service, but for the additional cost and complications in your network setup, it would be more beneficial to migrate your existing service into Office 365 or Google Apps for Business and gain several benefits you can leverage for your company. Syncing and sharing emails, contacts, and calendars are some of these features that hosted email providers typically do not offer their customers, along with a better built-in email filtering for ransomware attachments and phishing emails.
Risk of ransomware – in summary
The cost of being hit by one of these attacks can extremely pricey as it relates to actual dollars and the time spent recovering your data, but following these 10 simple guidelines above can prevent exposure to a ransomware attack, greatly minimize your risk, and even make recovery a much easier process.
Please reach out to us if you need assistance in assessing your network’s security, implementing any of the solutions from this article, or fixing a ransomware infection.



